Signal Processing
Written by Lorien Smyer
Thanks to Women Who Code, I was able to attend Twilio’s Signal Conference on May 24th and 25th, held at Pier 27 in San Francisco.
As a former bookkeeper who is gradually career-switching into web development, it can be tough to narrow down what tools to build applications with. I want to try all the things, but there just aren’t enough hours in the day. Conferences are a great way to get bite-sized introductions to various development tools and philosophies, and Signal was an excellent conference, with a wide variety of speakers on many interesting topics.
Tuesday started with a general session featuring Twilio cofounder and CEO Jeff Lawson introducing new products and various other speakers. I was impressed with how much live coding happened during the general session; it’s always fun to see talented developers in their element.
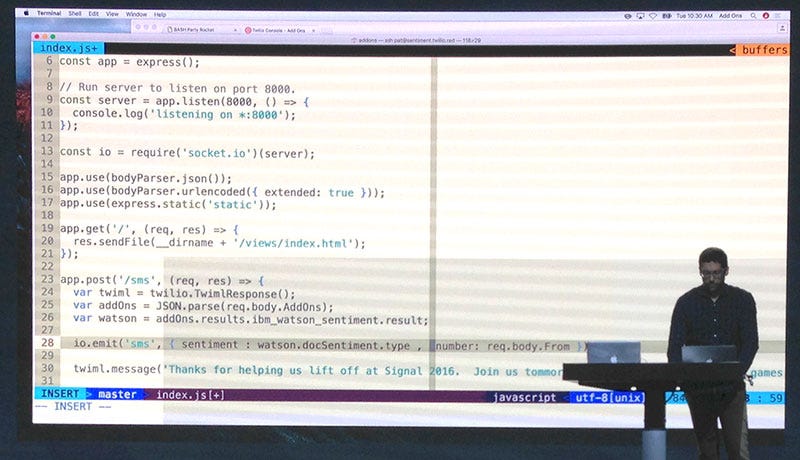
Patrick Malatack, Twilio VP of product management, demonstrating brand-new Twilio Add-ons
At lunch I sat outside at a picnic table with a group of young female developers. It was refreshing to hear them speak confidently and passionately about coding; aside from talk about how they knew each other (and a demonstration of a Ringly ring one young woman had on), all of the talk was about how they might be able to solve particular development issues that were cropping up at work.
After lunch the sessions began. There were usually six sessions happening at once, each from 35 to 50 minutes long, for a total of 47 Tuesday afternoon sessions. So many interesting choices!
The first session I attended was How to Build AWS Self-Service Through Delegated Identity Management, with Twilio infrastructure engineers Dom DeGuzman and Geoff Caton. I attended because I’m trying to learn more about AWS security and security in general, and because I’ve seen Dom speak quite a few times, and always enjoy her talks.

Twilio infrastructure engineer Dom DeGuzman (in very cool shoes)
Some of the main points were: to be sure to define and scope permissions, and to trust your infrastructure teams to be the only admins. They mentioned AWS Security Token Service as a useful resource; and Geoff also mentioned SAML, but commented that “there’s a lot of power with SAML that I didn’t explore” because “there’s a lot of XML and I don’t have that much time”.
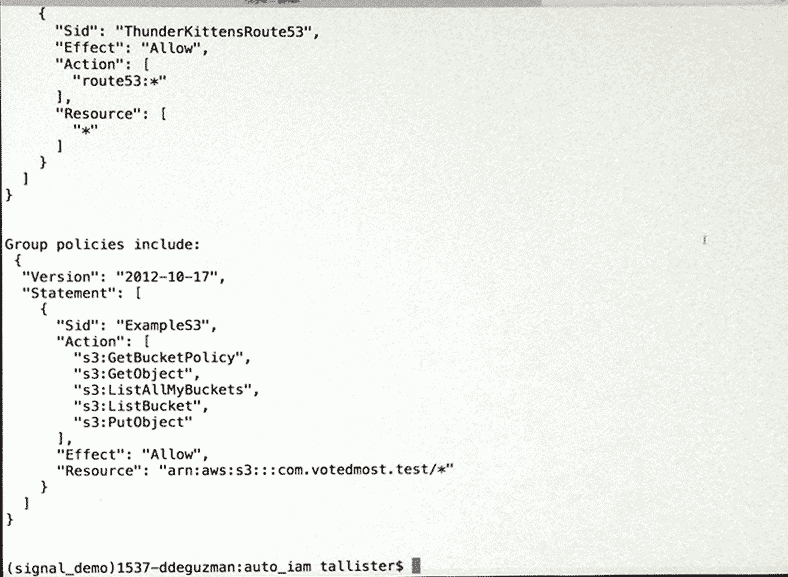
Example of what NOT to do from Dom DeGuzman
The next session I attended was Authy: Better Authentication for Your App in 30 Minutes, with Twilio’s director of product Simon Thorpe, and Authy’s lead solutions architect Dan Killmer. Authy’s two-factor authentication makes it possible to send a branded message with a lot of info to the user, and to include transaction-specific logos. It was a playful session, with Dan pretending to wire a million dollars to an audience member, whom he assumed had the phone number 867-5309.
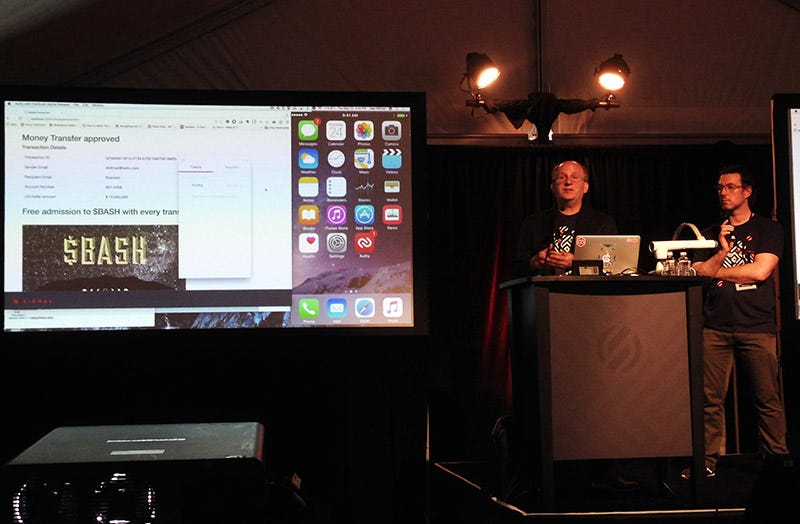
Dan Killmer and Simon Thorpe
After that was the session most personally useful to me, The Ins and Outs of Job Searching for Engineers, with Starfighter’s Patrick McKenzie.

Patrick McKenzie
His talk was encouraging, especially regarding speaking at conferences: he said “you can definitely talk at conferences”, that “people are starving for new voices”. He also said to make sure you get a copy of any videos of you speaking (there is no guarantee that a link to a video will be available forever), to archive your posts, and keep copies of any open source projects you contribute to.
Patrick described the typical hiring process in detail, and gave useful tips, including recommending cold email outreach to hiring managers (if done correctly).

Cold email tips from Patrick McKenzie
Next was WebTorrent — Bringing P2P to the masses with WebRTC, with WebTorrent developer Feross Aboukhadijeh. WebTorrent is written completely in JavaScript, and is the first torrent client client that works in the browser. It uses WebRTC instead of TCP/uTP as the transport protocol.
While I’m not that familiar with P2P computing, I’m starting to become more interested in the subject of decentralizing the Web. Feross’ session on WebTorrent was both impressive and approachable.
At 4:15pm I attended Developing Good Slack Apps and Custom Integrations, with Slack associate frontend engineer Allison Craig.

Slack associate frontend engineer Allison Craig
Continuing the playful theme so prevalent in the Signal talks I attended, her demo app was called Bottie McBottface. Some of her tips included:
* Concise install page:
* Tutorials
* Gifs that show how users can interact with your app
* List of commands
* Digest, don’t spam:
* Don’t DM everyone; only message people you have to
* Consider the use of emojis:
* For example, a weather app could use emojis; then you don’t have to translate into other languages
Next was Secure Payments Over Mixed Communication Media, with PayPal’s head of global developer advocacy Jonathan LeBlanc. Topics he covered included passive identification (building up little bits of information to validate a user), and asynchronous cryptography (using public and private keys).
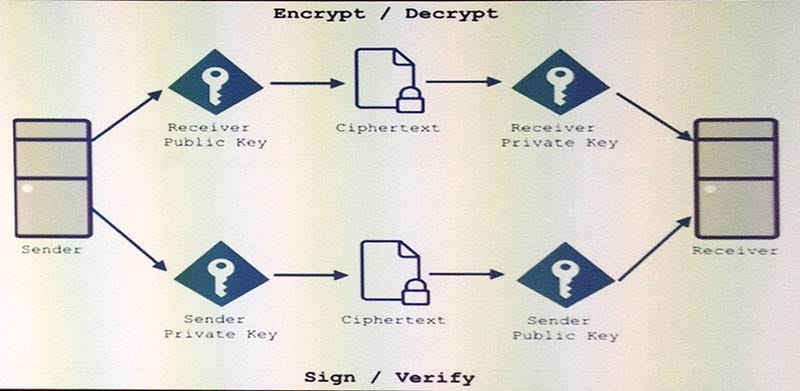
Asynchronous Cryptography
At 5:25pm I attended WebRTC Hacks: Lessons Learned with Chad Hart, an independent consultant in marketing and product management, and the chief editor of webrtcHacks.com.
Chad went to school for electrical computer engineering, but doesn’t program professionally. All of the projects he described he built for personal practical purposes, including:
A monitor to detect when his toddler daughter was silently getting up after her nap (since a regular baby monitor couldn’t detect her movement)
An automated robot to (gently) get his dog off of the family’s new couch
A refrigerator camera that could detect when someone four years old or younger was looking in the fridge (when his young daughter was insisting that she hadn’t been leaving the fridge door open)
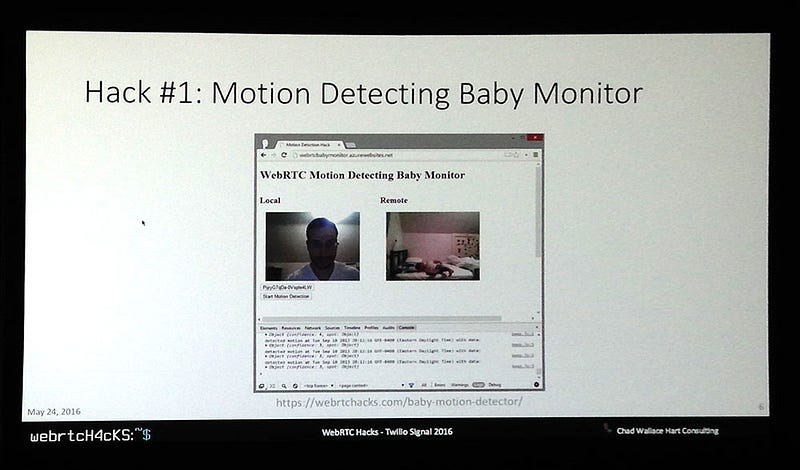
Chad Hart’s Baby Monitor project
For the last session of the day I attended Using Real-time Voice Masking to Take Gender Off the Table in Technical Interviews, with Aline Lerner, founder of interviewing.io. Interviewing.io is part of the promising new field of anonymous interviewing in tech; as Aline said, “most of our customers care very deeply about gender bias”. The one factor that is not anonymized on the platform is voice, so they built a real-time gender-masking voice modulator to investigate the effect of gender on interview outcome.

Aline Lerner, founder of interviewing.io.
The surprising result was that removing gender from the interviews (as best they could) did not increase the success of female candidates. This result made them look deeper into the question of why women weren’t succeeding at the same rate as male candidates, and they found that “it seemed like there were a lot more women who would quit after one bad interview”, despite their “failure and shame being completely private”.
I found this to be good news; while it’s no fun to fail at an interview, and I personally have experienced that strong desire to opt out of the interview process after an unsuccessful attempt, personal resiliency is easier to correct for than systemic sexism.
Following the sessions was a reception in the community hall, where I met developers from the Midwest on a quest for sushi (not widely available in their very landlocked community), and completed the amusing button-collecting quest that Twilio had developed for the conference.

Button-collecting quest at Signal
While I was collecting the buttons, I also found out about a volunteer program run by Twilio that looks very interesting:

Text “Do Good” to Twilio to let Twilio.org know you want to use your skills to help nonprofits
Wednesday, like Tuesday, began with opening remarks featuring Twilio CEO Jeff Lawson. A highlight for me was his Q & A (via remote video) with Rony Abovitz, the founder of Magic Leap, a mixed-reality technology company that appears to be working on some very exciting things. As a gamer, movie enthusiast, and developer, I am keenly interested in the possibilities of AR/VR/MR, so it was fun to learn about another big player in the field.
I must confess, I left the opening remarks early because the DocuSign booth was raffling off a drone, and you had to be present to win. I don’t even know if I want a drone, I just like winning stuff, and I was glad that a young woman who says she usually doesn’t win things won the drone. I had a great time talking with the DocuSign folks while waiting for the raffle to begin. However, I was sorry to have missed any part of the opening remarks; fortunately, a video is available.
Once again there were 47 sessions to choose from; for my first session of the day I picked Privacy and Security: Trends in Technology Policy and Advocacy. This session had four panelists: Nate Cardozo, staff attorney with the Electronic Frontier Foundation, Michelle Paulson, legal director of the Wikimedia Foundation, Sheila Jambekar, associate general counsel at Twilio, and Evan Engstrom, executive director of Engine. The panel was moderated by Ben Kepes.

Privacy and Security: Trends in Technology Policy and Advocacy panel
The point that stuck with me the most from the panel was: protect the users of your products by being very selective about what data of theirs you keep. As Sheila said, “it’s not just data, it’s someone’s data”. Nate said if you’re not sure whether you need to comply with a request for someone’s data, you can contact the EFF and they may be able to help. Michelle advised “if you’re not already doing this, HTTPS for everything”.
After lunch was HTTP/2 and Asynchronous APIs, with Davey Shafik, developer evangelist for Akamai. He kept us engaged with lines like “HTTP2: we know it’s real because it has a logo”, and “the point is that HTTP1 sucks”. The bottom line for HTTP2: “there are huge performance wins unless you do it wrong”. He said a lot more good stuff, but this post is getting long, so check out his slides
.
Next I attended Capturing and Rendering Video on iOS, with Twilio iOS video SDK engineer Chris Eagleston. A lot of his talk was about RGB vs YUV (which he said webRTC uses pretty much everywhere).

Twilio iOS video SDK engineer Chris Eagleston
Chris said that the human eye is sensitive to changes in brightness, but much less sensitive to changes in color, and that YUV has a size savings over RGB by having fewer rows of color channels, with the top four rows of a YUV frame showing brightness. He also gave us a link to a GitHub repo of a sample Swift app that demonstrates advanced Video Capture and Render techniques with the Twilio Video SDK for iOS.
At 2:35pm was the session I found to be most inspiring, Mobile Phone Technology for Health in Africa, Opportunities for a Healthier Continent, by Dr. Precious Lunga, head of health at Econet Wireless.

Dr. Precious Lunga, head of health at Econet Wireless
As Precious told us, she has “seen how mobile phones have just proliferated throughout the whole continent”: mobile phone penetration is at 98% across the African continent, and in two to five years, most people will have smart phones, because they are replacing their older phones with smart phones when the older phones break. In Africa, if you have a phone number, you have access to services; mobile phones are a lifeline.
Precious is part of a company getting health information to people through SMS. It started out as a pilot project; they were aiming for 10,000 users in the first year, but within six months they reached half a million subscribers.

Econet Wireless Health Tips Service
Precious spoke about a woman who told her that the messaging service saved her daughter’s life. Her young daughter was ill and becoming dehydrated from her symptoms; the mother didn’t know what to do, nor did her neighbors have any practical advice. Fortunately, she was a subscriber to the health messaging service, and through it found out about a re-hydration solution she could make.
Another innovation Precious talked about is a system to store vaccines for babies in small refrigerators next to mobile phone base stations. The fridges tap a tiny bit of power from the base stations to run, and nurses are sent SMS messages if a fridge breaks down, or vaccines are running low. This brilliant idea makes it much more likely that babies get vaccinated at the right time.

Energize the Chain project, with vaccine fridges powered by mobile phone base stations
The next session I attended was more prosaic, but also useful: Usable Ops: How to Make Web Infrastructure Management Easier, with Joyce Jang, engineer at Hearsay Social, and software engineer Kate Heddleston.

Joyce Jang and Kate Heddleston
As Kate said, “it’s difficult to train engineers in a reasonable amount of time if your system is too complex. Usability is all about making the right things easy and the wrong things hard”. Kate suggested using containers such as Docker to improve usability. Joyce advised making sure your devs can’t do things like erase your entire database; to “build good abstractions”.
At 4:15pm was one of the best-attended sessions, Terrible Ideas in Git, by Corey Quinn, director of devops at FutureAdvisor.

Corey Quinn speaking on Terrible Ideas in Git
I’m guessing the amusing session title attracted attendees, and they were not disappointed. With lines like “most of us aren’t committing large binaries after the first time we do it”, “I’m a Full-Stackoverflow developer” and “a group of developers is called a merge conflict”, Corey kept us laughing and learning.
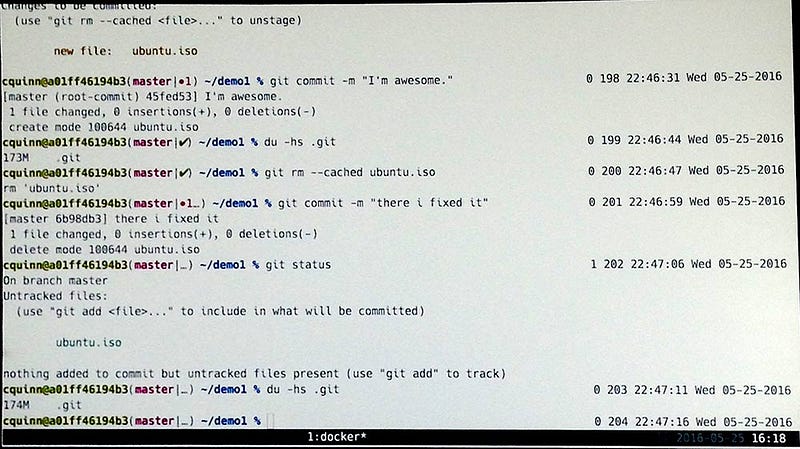
Example of what NOT to do in Git
Next was another fun and informative session, Speaking at Career Day, with Wedgies full stack developer and cofounder Jimmy Jacobson.

Jimmy Jacobson giving his career day presentation
Jimmy has three daughters, and has developed a presentation for speaking at their career days. He gave us the actual talk he gives the young students, with some asides to let us know how the students react. For example, they recognize the Mario background on his slides: “all the kids, somehow, still play Mario”; and when he asks for questions after the talk, they ask things like “do you play Minecraft”.

Slide from Jimmy Jacobson’s career day presentation
Jimmy’s talk included resources to share with kids to help them learn to program:
Codecademy
Khan Academy
Scratch (useful for live-coding during presentation)
CodeCombat
He encouraged the audience to give presentations to kids: “a lot of kids don’t grow up with programmers in their families, so they don’t know it’s a job they can have”.
The last session of the day was another personally inspiring one for me: Technical Blogging to Build Your Digital Presence, by iOS developer and Access Code 2.2 alum Ayuna Vogel.

Ayuna Vogel speaking on Technical Blogging
A year ago she didn’t know how to code, and here she was, speaking at Signal. She encouraged all of us to write technical blog posts: “nobody knows everything, there is always something you can share”, “if you have a problem, someone else has the exact same problem”, and “you will go back to your own blog post for your own reference”.

Blogging tips from Ayuna Vogel
While I was thankful for her specific tips, the best part of her talk was just seeing her up there, speaking. She made me feel like perhaps, I, too, could speak at a conference.
Immediately following the last session of the day was Signal’s $BASH party. It was held in the same tent the general sessions had been held in, but transformed with a large variety of creative food stations (including liquid nitrogen ice cream and popcorn), a DJ on the big stage, and an inventive number of space-themed carnival games, with prizes like a do-it-yourself ghost chili hot sauce kit, and Star Wars ice cube trays /chocolate molds.
My favorite game was one in which you had to reassemble a partially disassembled computer (re-seating memory, reattaching hard drive, etc.); power it up, then print “Hello World” to the terminal.

Computer assembly and coding challenge at Signal’s $BASH party
It was a timed challenge, with three stations so three people could play at once; but you were only competing against yourself, so contestants voluntarily helped each other succeed.

Happy me after I completed the computer assembly and coding challenge. (I’m not usually fuchsia, it was just the cool party lighting.)
Collaboration and encouragement seemed to be a large theme at Signal; I felt welcomed and encouraged throughout the conference, and would recommend any beginning developer who has the opportunity to attend next year to jump at the chance.
